
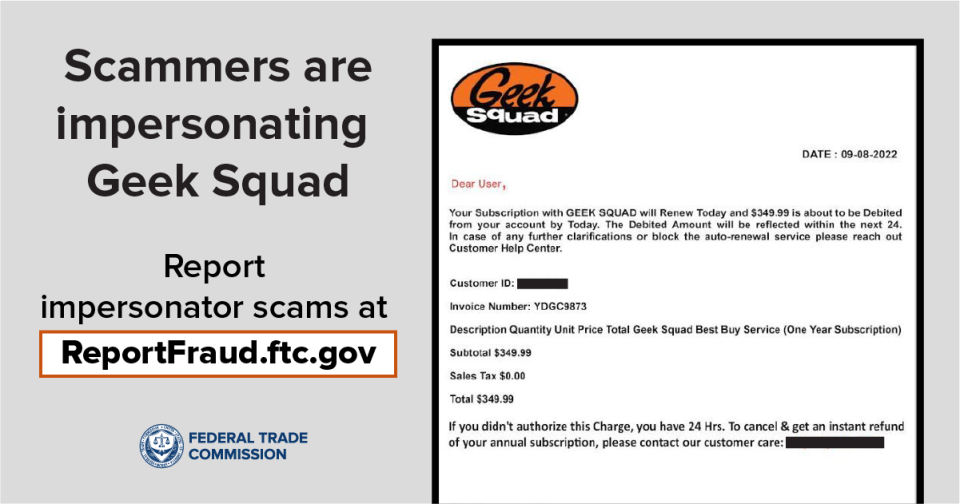

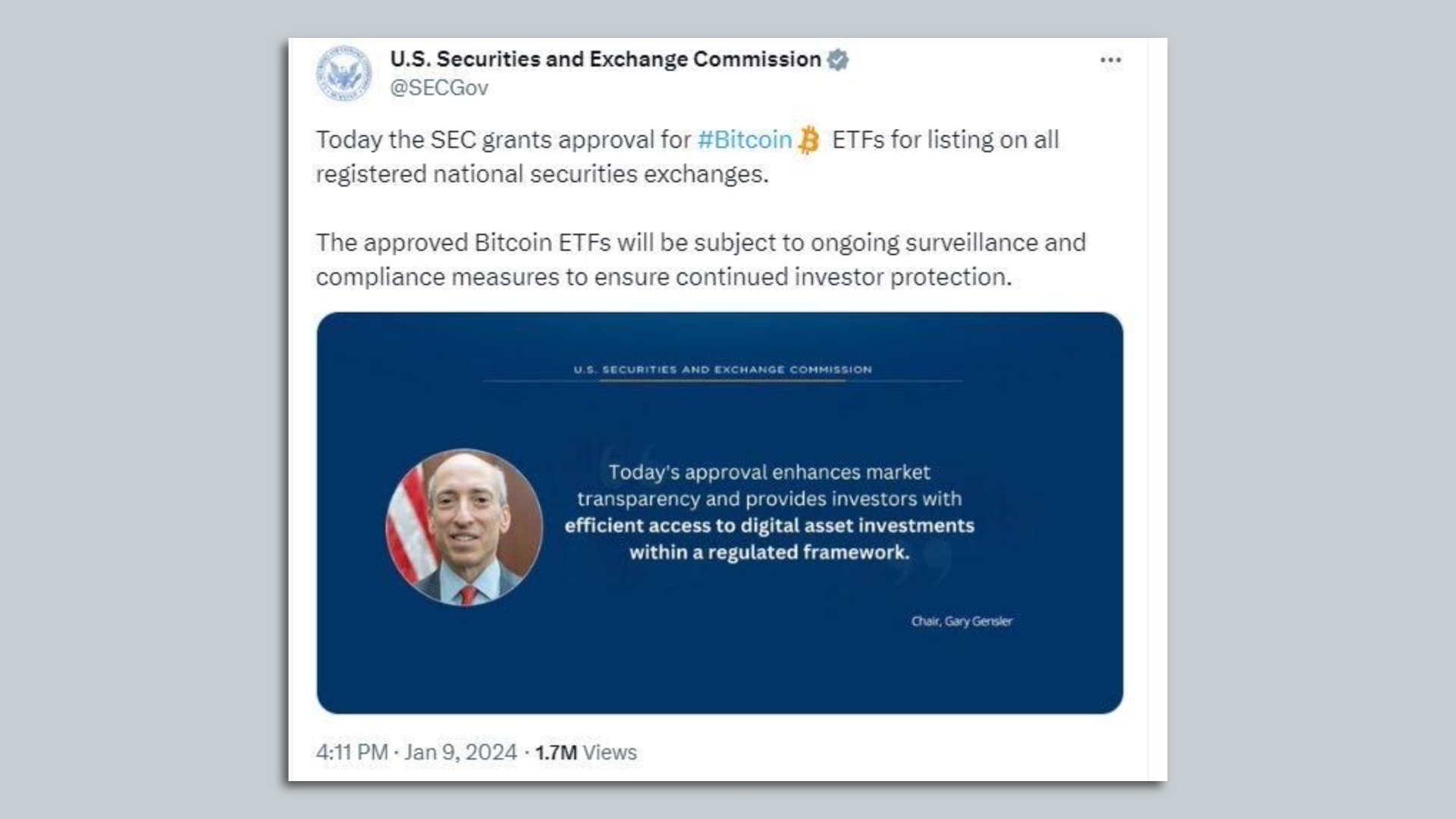
Smart Contract Upgrade Scam Explained: How “Protocol Updates” Are Used to Steal Crypto
The smart contract upgrade scam is a crypto fraud that exploits users’ trust in routine protocol updates. Victims are told that a platform, wallet, or protocol requires an urgent “upgrade” to continue operating safely. In reality, the upgrade is fake — and approving it gives scammers control over the victim’s wallet or tokens.
This scam is especially dangerous because upgrades are a normal part of blockchain ecosystems, making the request feel legitimate.
What Is a Smart Contract Upgrade Scam?
A smart contract upgrade scam occurs when scammers:
- Claim a protocol or contract has been updated
- Urge users to “migrate,” “upgrade,” or “re-authorize” assets
- Present an approval request disguised as maintenance
The user believes they are keeping their assets safe, but instead grants malicious permissions that allow funds to be drained.
How the Smart Contract Upgrade Scam Works
Step 1: The Upgrade Announcement
Victims are notified through:
- Fake websites
- Impersonated social media accounts
- Direct messages
- Email or chat alerts
The message often stresses urgency or security risk.
Step 2: Wallet Connection Prompt
Users are instructed to:
- Connect their wallet
- Confirm ownership
- Prepare for the upgrade
Everything appears routine.
Step 3: Malicious Approval
Instead of a genuine upgrade, the site requests:
- Token spending approval
- Asset transfer permission
- Unlimited access authorization
The approval message looks technical and confusing.
Step 4: Asset Drain
Once approved:
- Tokens are transferred out
- NFTs are moved
- Stablecoins are drained first
- Losses occur rapidly or after a short delay
The “upgrade” never existed.
Why This Scam Is So Effective
Smart contract upgrade scams work because:
- Real protocols do issue upgrades
- Security-themed messages create fear
- Technical language discourages questions
- Users believe they are preventing loss
- Wallet prompts look legitimate
Fear + urgency = fast approval.
Common Variations of the Scam
“Emergency Security Upgrade”
Victims are told assets are at risk unless upgraded immediately.
“Contract Migration”
Users must move funds to a “new” contract.
“Version Update”
Old contracts are said to be deprecated or unsupported.
“Compliance Upgrade”
Victims are told regulations require re-authorization.
All lead to the same outcome: loss of funds.
Warning Signs Most Users Miss
- Upgrade notices sent privately
- No public announcement outside the link provided
- Requests for approvals instead of migrations
- Pressure to act quickly
- Claims that funds will be lost if ignored
Legitimate upgrades are transparent and verifiable.
Smart Contract Upgrade Scam vs Legitimate Upgrades
Legitimate upgrades:
- Are publicly announced
- Do not require surprise approvals
- Provide clear documentation
- Allow users time to act
Scam upgrades:
- Use urgency and fear
- Hide behind fake interfaces
- Request unlimited permissions
- Offer no verifiable proof
Transparency is the key difference.
Who Is Most Targeted
This scam often targets:
- DeFi users
- NFT holders
- Active traders
- Wallet users with large balances
- Victims of earlier crypto scams
Attackers look for users likely to respond quickly.
What To Do If You See an “Upgrade” Request
If you encounter an upgrade notice:
- Do not approve anything immediately
- Avoid clicking links sent privately
- Verify announcements independently
- Never approve permissions under pressure
Pausing for verification prevents irreversible loss.
Final Thoughts
The smart contract upgrade scam weaponizes trust in routine blockchain maintenance. By disguising theft as security, scammers convince users to hand over control willingly.
In crypto, real upgrades are transparent and patient.
If an “upgrade” demands speed, secrecy, or blind approval, it isn’t protecting your assets — it’s targeting them.